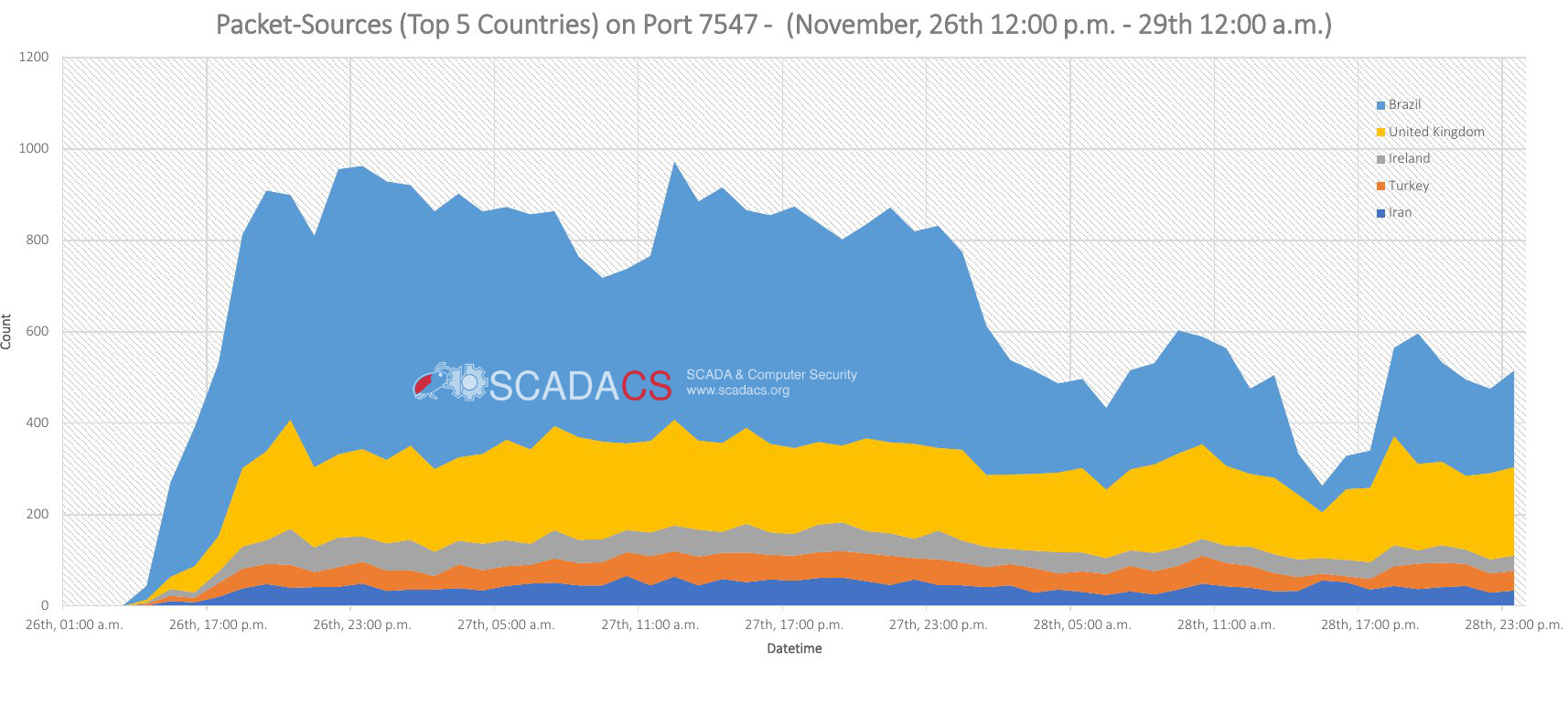
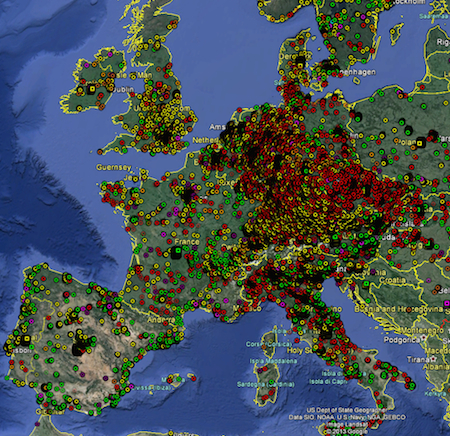
TR-069: Before and after the 2016/11 botnet attack that caused the Telekom AG outage in Germany.
Using data from censys.io and our data enrichment and analysis framework from the RiskViz project, we are able to show the distribution off all TR-069 devices in Europe before and after the attack. It is very easy to see that the Telekom attack has blocket the TR-069 TCP-Port 7547.

Reachable TR069 devies in europe (30.11.2016)
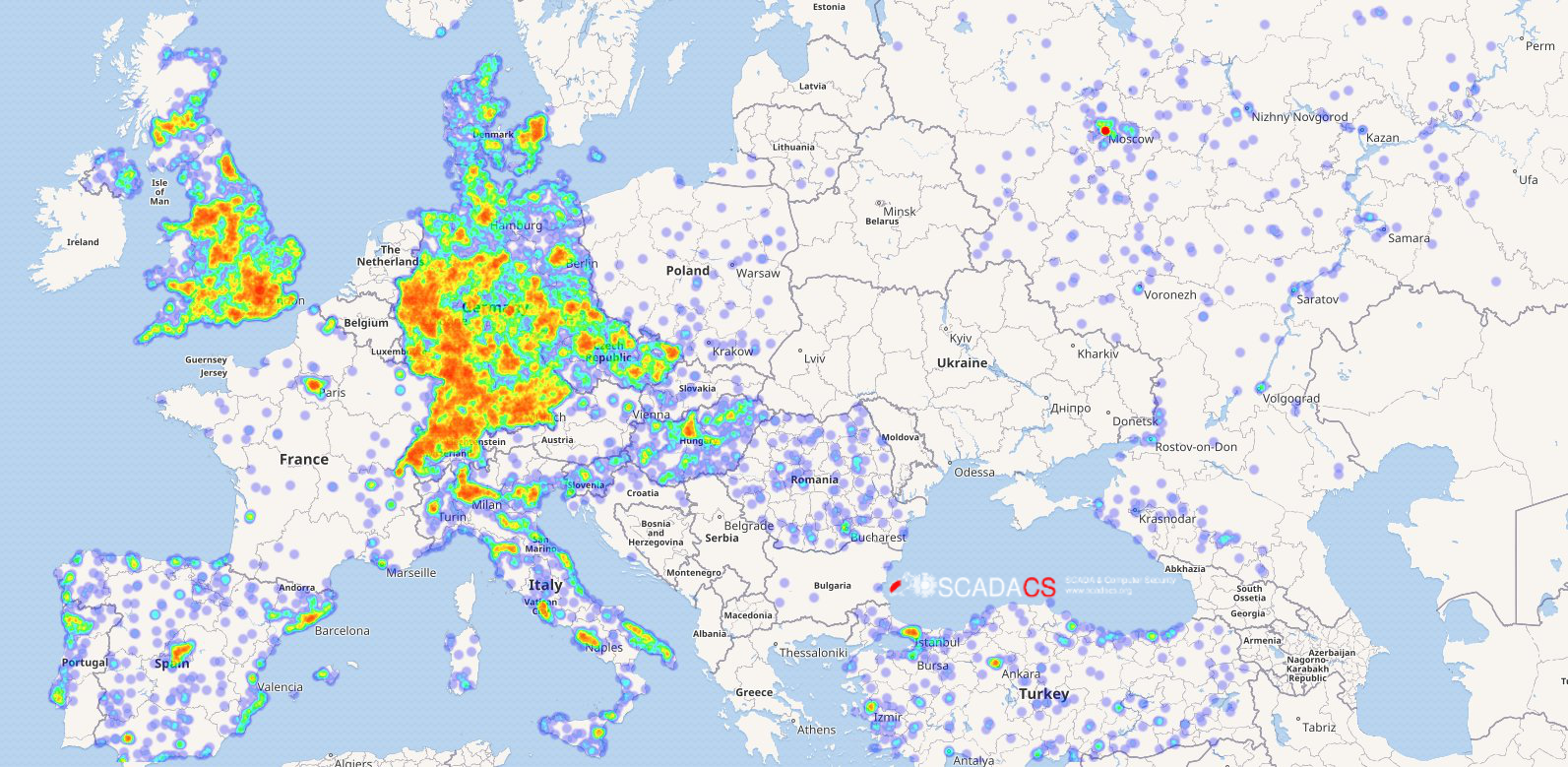
Reachable TR069 devices in Europe (23.11.2016)
The Analysis of our university darknet shows that the most scan traffic was originated by Brazil, UK and Ireland.